Service Process
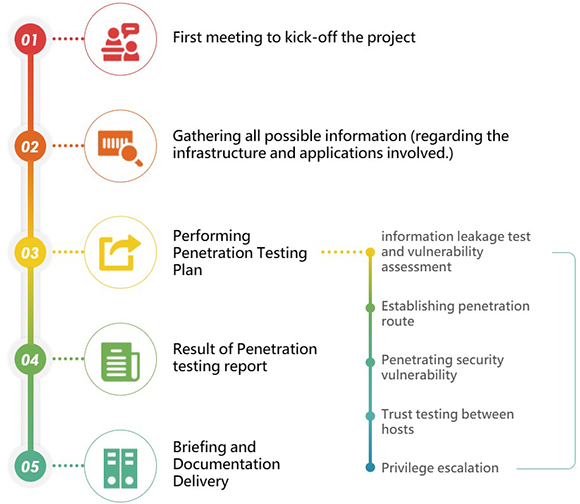
To conduct penetration test, our IT staff simulates real hackers in order to challenge the system’s protection mechanism, such as agency server, host operating system, applications, Internet service and IoT device that is equipped with IP. We try to obtain unauthorized authentication and work on privilege escalation to check whether the internal information has been improperly exposed, tampered or stolen. We aim at finding out the security blind spots and patch the flaws to reduce security risk. After this, re-assessment will be provided in order to make sure all the vulnerabilities have been remedied.
Vulnerabilities in the operating system
Applications:
email service, website service, file archive service, remote connection service, network service, etc.
Website service:
Configuration management, User authentication, Connection management, User authorization, Logic vulnerability, Input validation, Web service, Ajax and other categories.
Password cracking: testing the strength of password.
A.Information gathering
After collecting data, we analyze the target firmware and the service it uses, such as https, in order to examine vulnerabilities existing in the service itself. Relevant information will make reference to penetration test.
|
B.Risk Management
Before executing penetration test, it is recommended to back up data within the tested target to avoid unexpected information damage or data loss. During the execution of penetration test, the implementation of intrusive testing operations must be confirmed with the corporation. Relevant testing operations are only carried out when it is at the appropriate time agreed by both parties with proper contingency measures and risk evaluation.
|
C.Testing Result
We provide test results for all testing items in terms of the service description (the actual testing items are mainly based on the services provided by the host or website under test). Detailed process and content will be explained, which includes target detection, vulnerability name, problematic URL or IP, problematic parameters, etc. The potential risk they might cause will be explained further.
|
D.Analysis report
According to the testing result, general process and vulnerabilities that are discovered are recorded in detail with pictures as the evidence of the process and result. The results will be confirmed in order to reduce the misjudgment problems (such as false positive, false negative). Finally, we will put forward relevant suggestions and testing reports.
|
