Key-Reporter Vulnerability Assessment Reports Management System
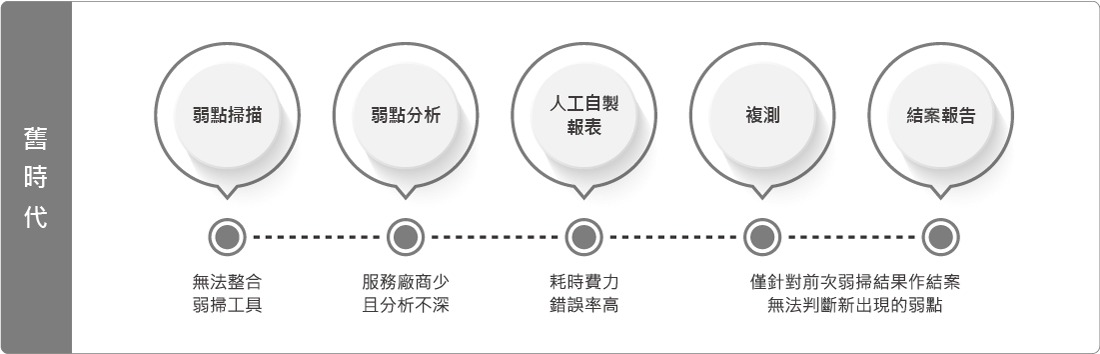
Key-Reporter makes vulnerability management become a continuous and dynamic process by focusing on the management of the process of handling vulnerabilities after they are discovered and combined with the automatic assignment.
What Key-Reporter can do for you
Key-Reporter provides an automated vulnerability management process to improve the security performance of enterprises.
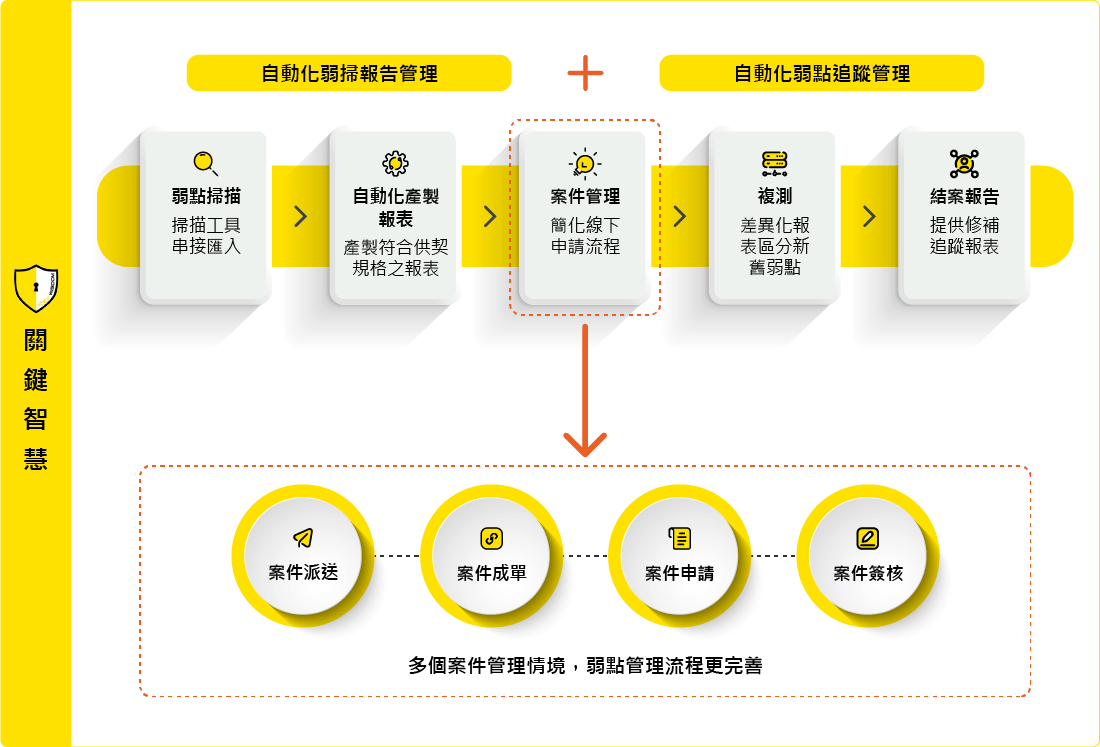
With its one-stop functionality, Key-Reporter allows customers to scan for vulnerabilities and analyze them, as well as to follow up and close cases.
Key-Reporter Features
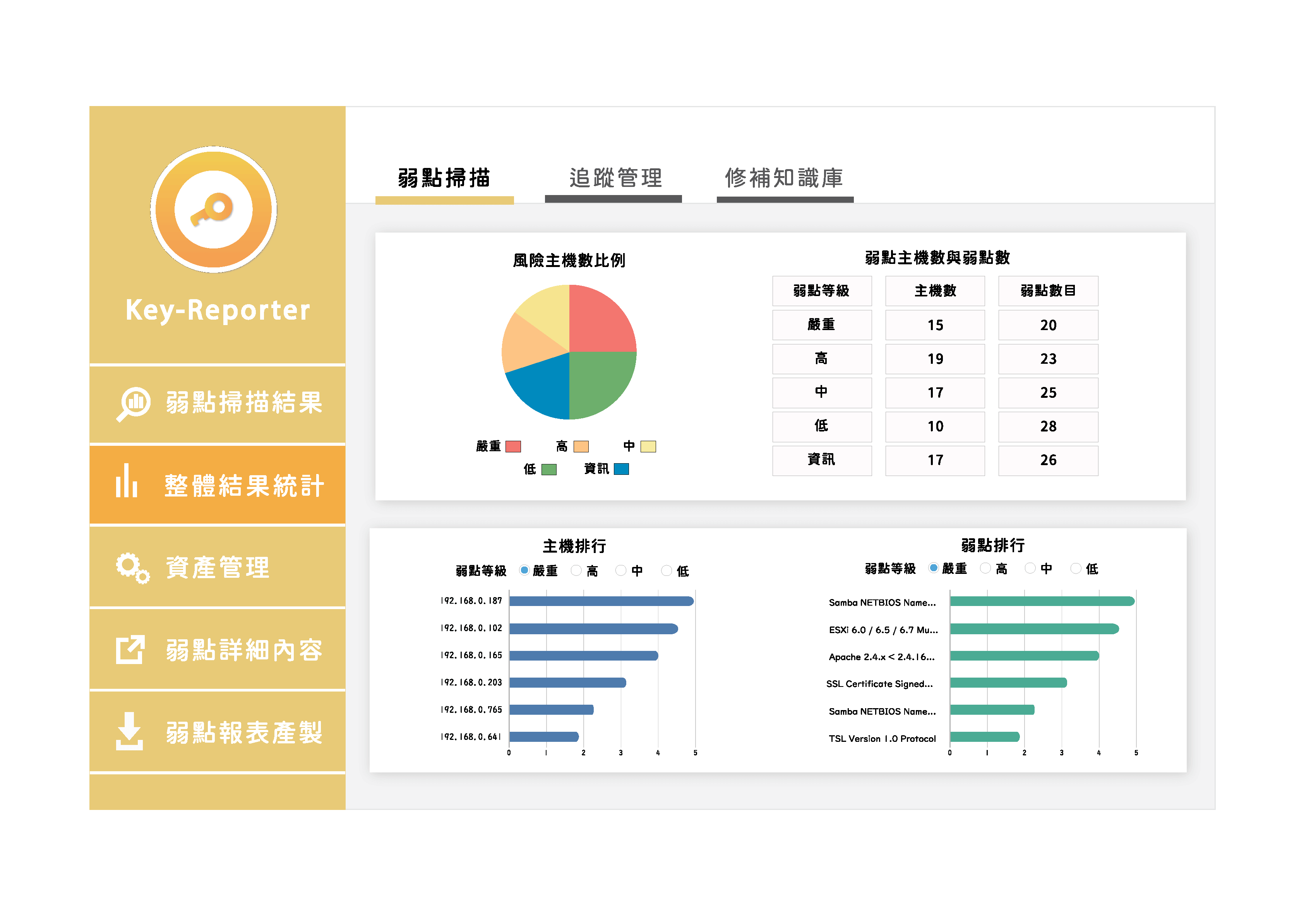
Report
Compared to other vulnerability assessment report management systems in the market, Key- Reporter can generate the scanning reports in, 10 minutes, and based on the analysis of scanning results provide an effective and complete patch to fix the vulnerability.

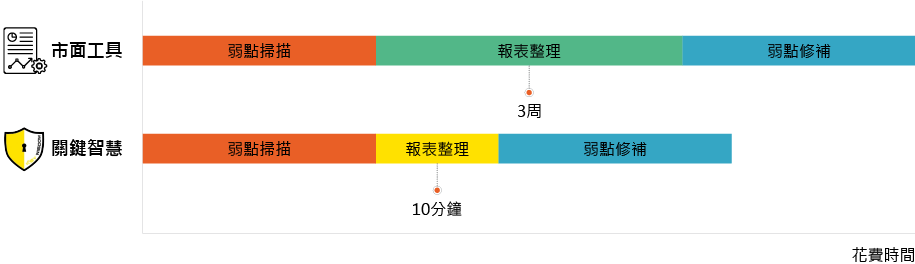
For IT staff, the time saved can be focused on vulnerability remediation and improving vulnerability consulting capabilities. IT managers can also get a vulnerability report on the same day that the scan is completed so that they can quickly understand the status of the vulnerability and distribute the fixes.
Import
Key-reporter is designed to be connected to global famous scanning tools, i.e. Tenable and Rapid7, and supports the import of different types of scan results, such as system vulnerability scans, web vulnerability scans, penetration tests, and code review scan reports.

By generating a report through Key-Reporter, users can have an optimized version of the original reports on the dashboard.
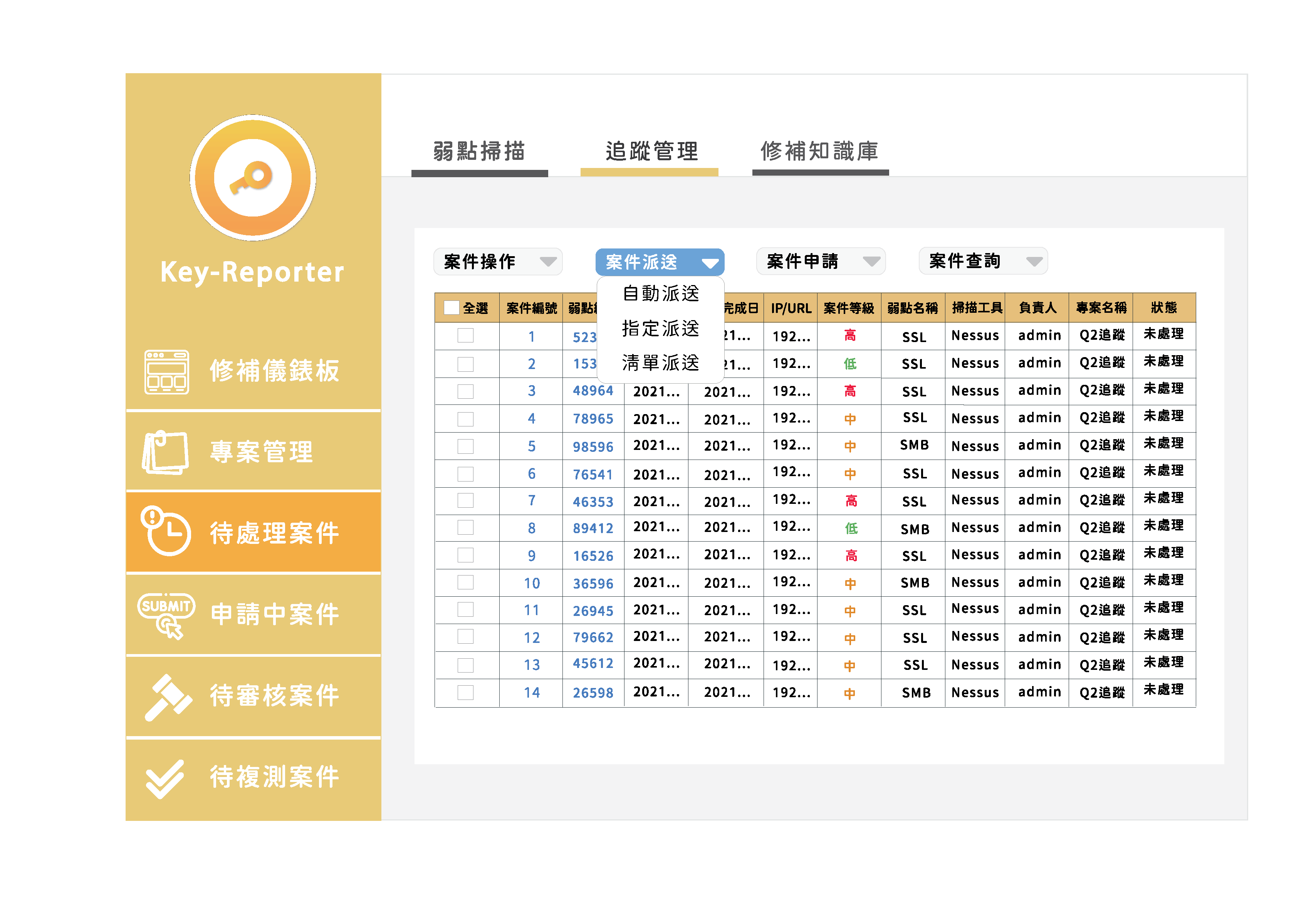
Send
Once a case has been established, the system will send the case to the corresponding IT staff by matching the asset information. In the case of failed dispatch or special circumstances, the option to specify a dispatch is also available.
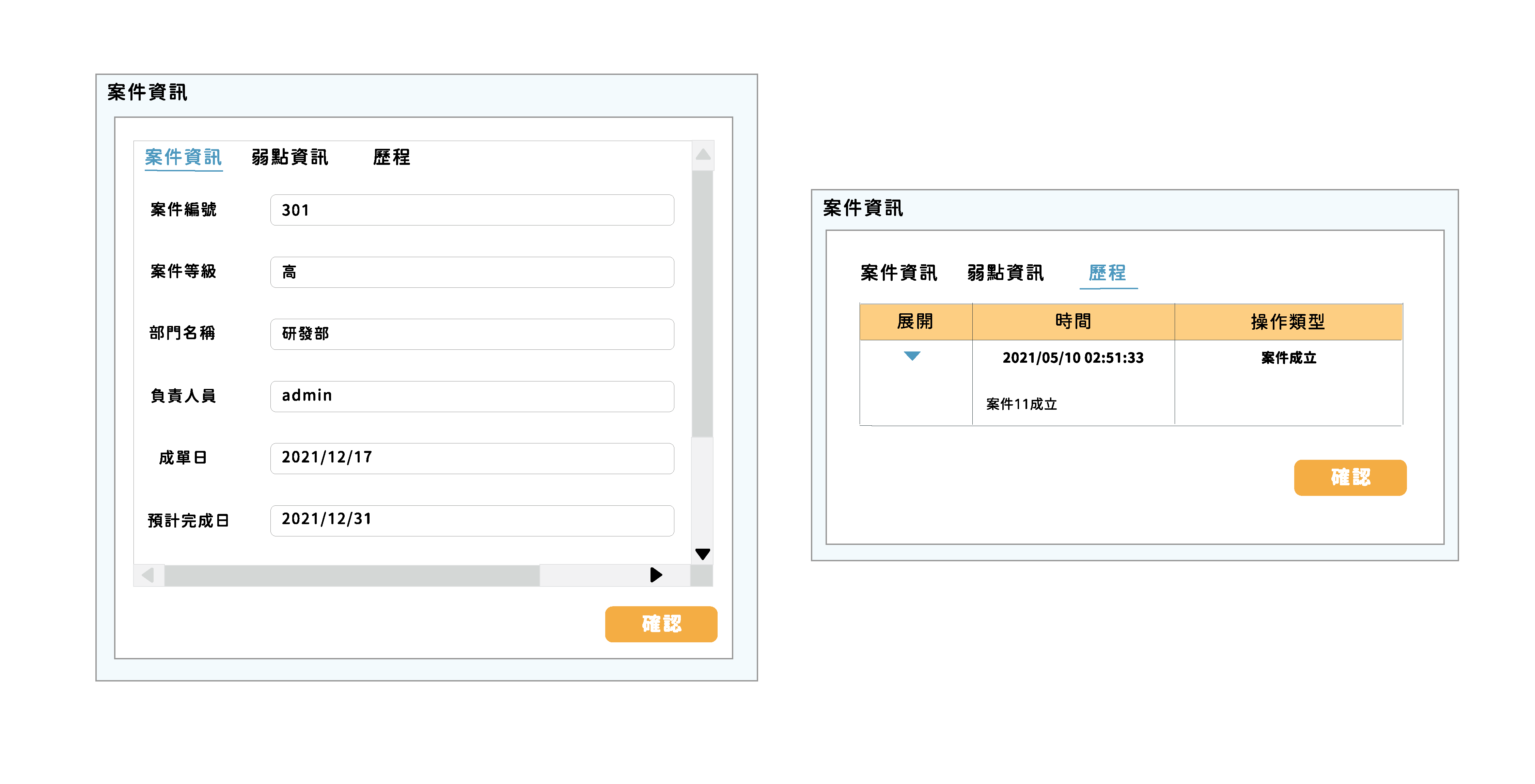
Set Up
The person in charge can set a range of dates for case completion based on the level of the case.
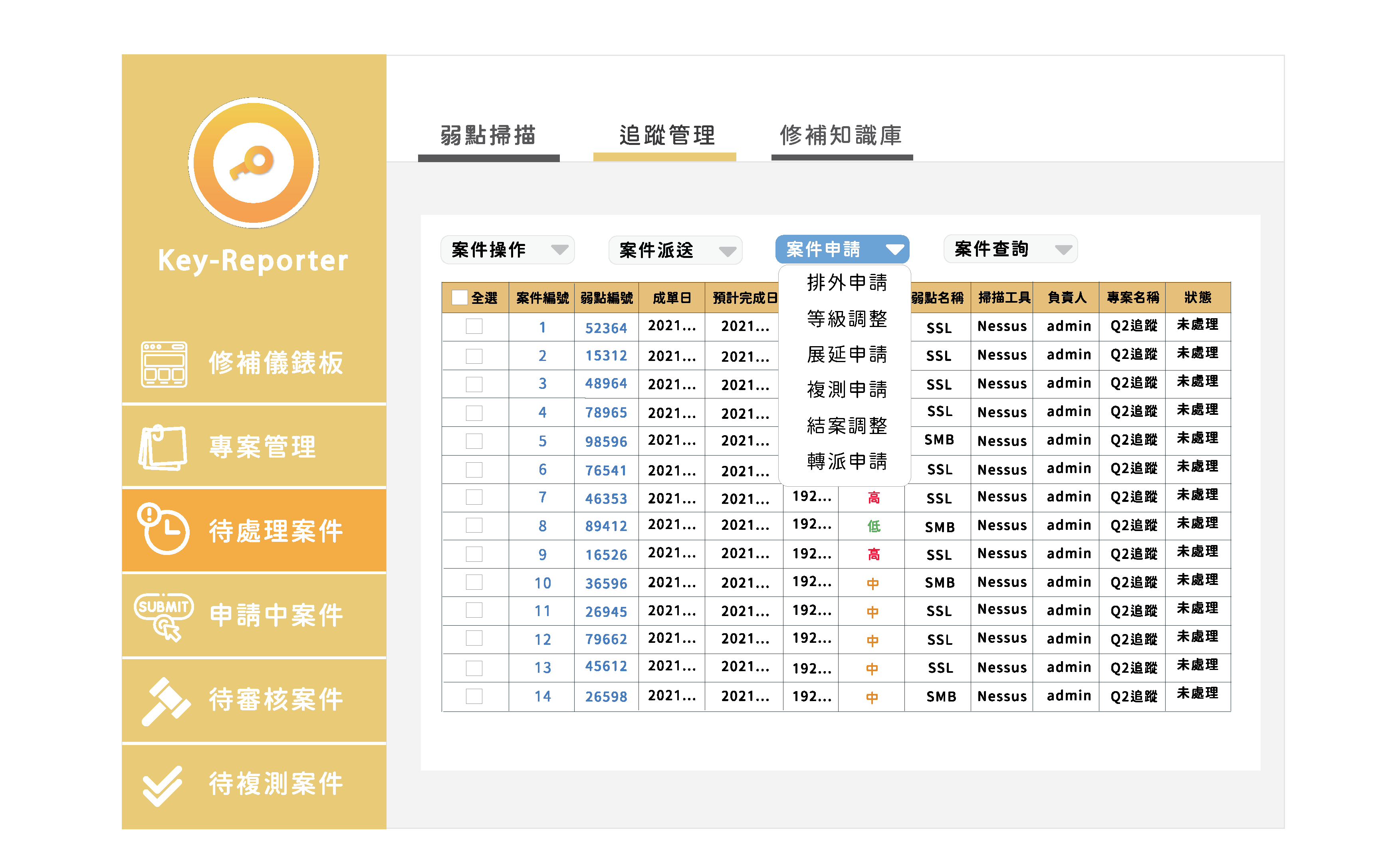
Apply
In contrast to the previous way of processing applications offline, which led to scattered e-mails and attachments, Key-Reporter allows you to complete the status of all cases, including exclusions, extensions, retests, closings, and reassignments. The system also allows you to check multiple cases for applications and apply the same application instructions to multiple cases.
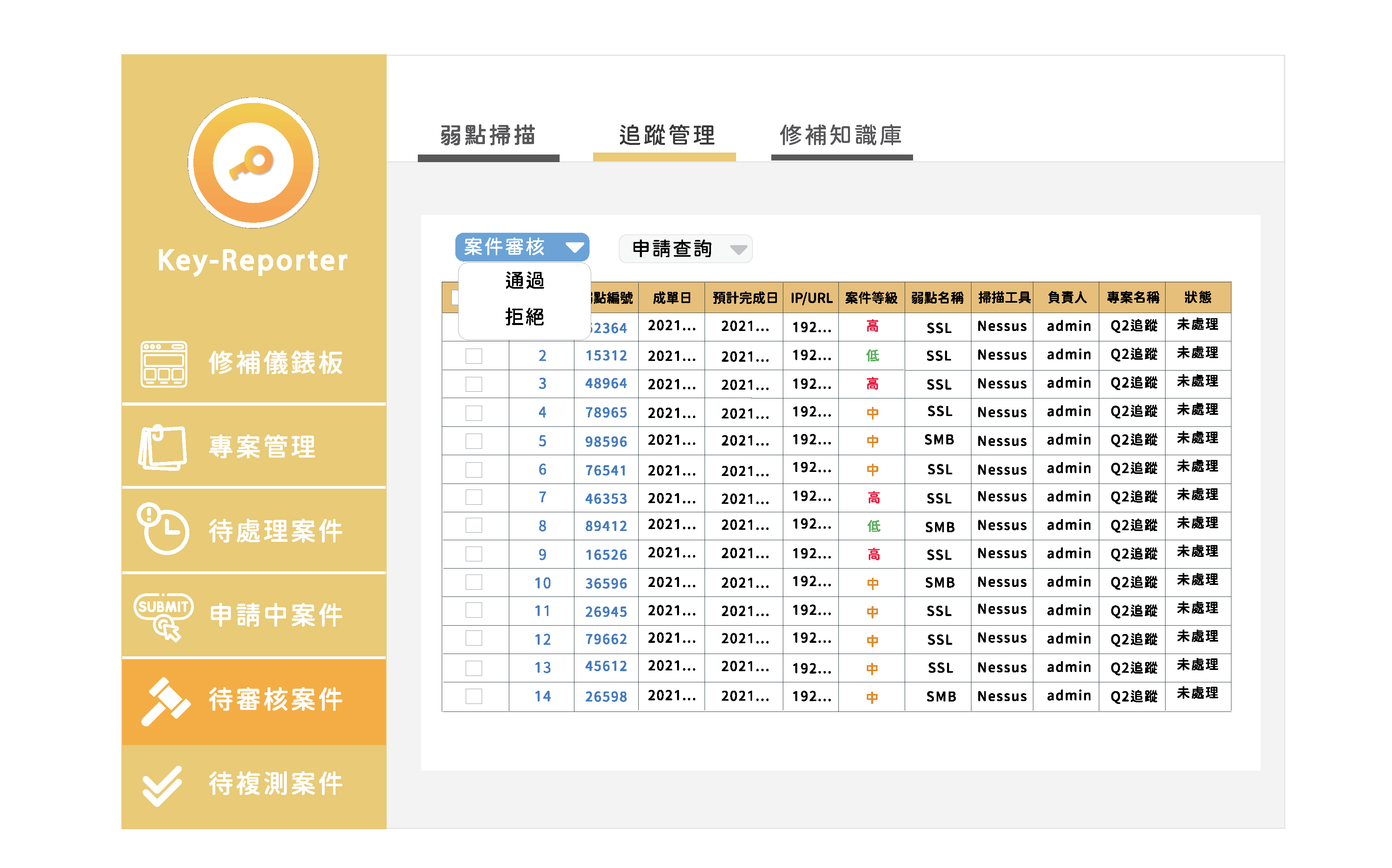
Approval
You can see the current applications that need to be validated under ‘Pending Cases’.
Retest
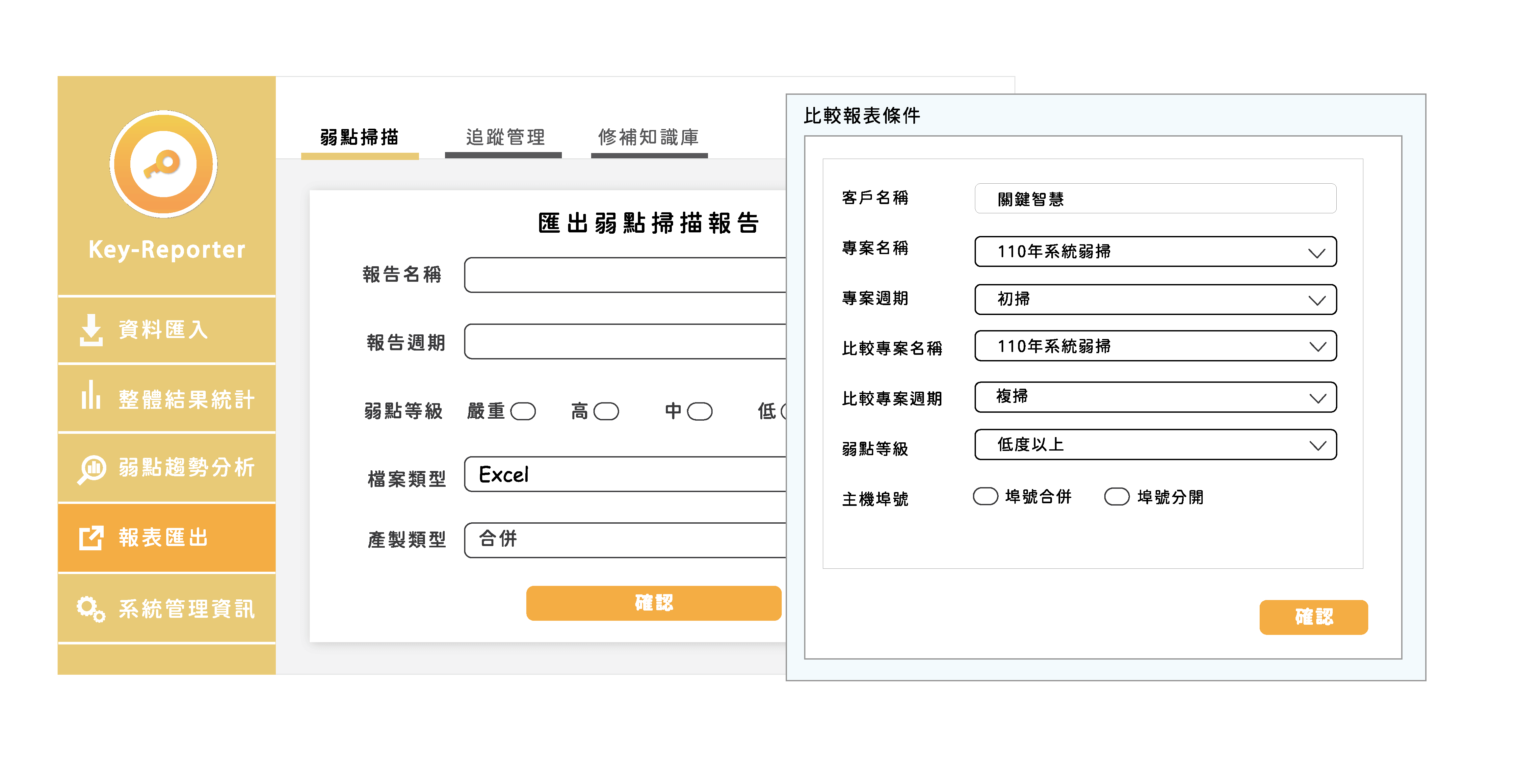
If a request is made for a retest, the system will automatically compare the initial and repeat scans and provide a comparison result.
Closure
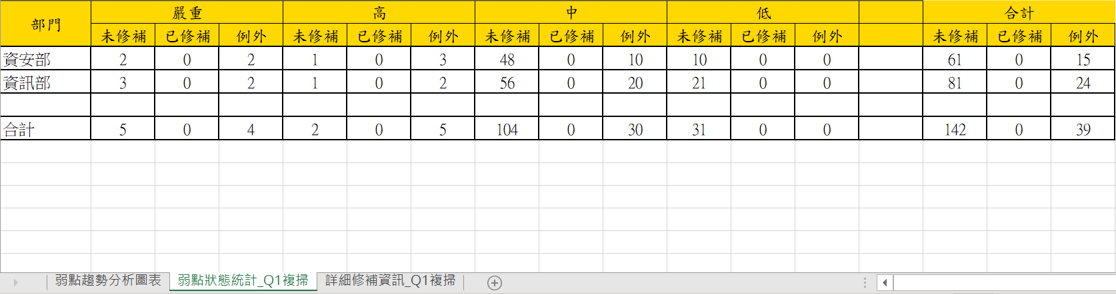
Once the weaknesses have been fixed, a closure request is made to change the status of the case to closed and a tracking report is generated to provide statistics on the status of the vulnerability fixed by department and level for different project cycles and to compare the changes in the number of vulnerability across multiple projects.
● 弱點趨勢分析圖表:比較多個專案的弱點數量變化

● 弱點狀態統計:針對不同專案週期,統計各部門、各等級的弱點修補狀況
Consultancy
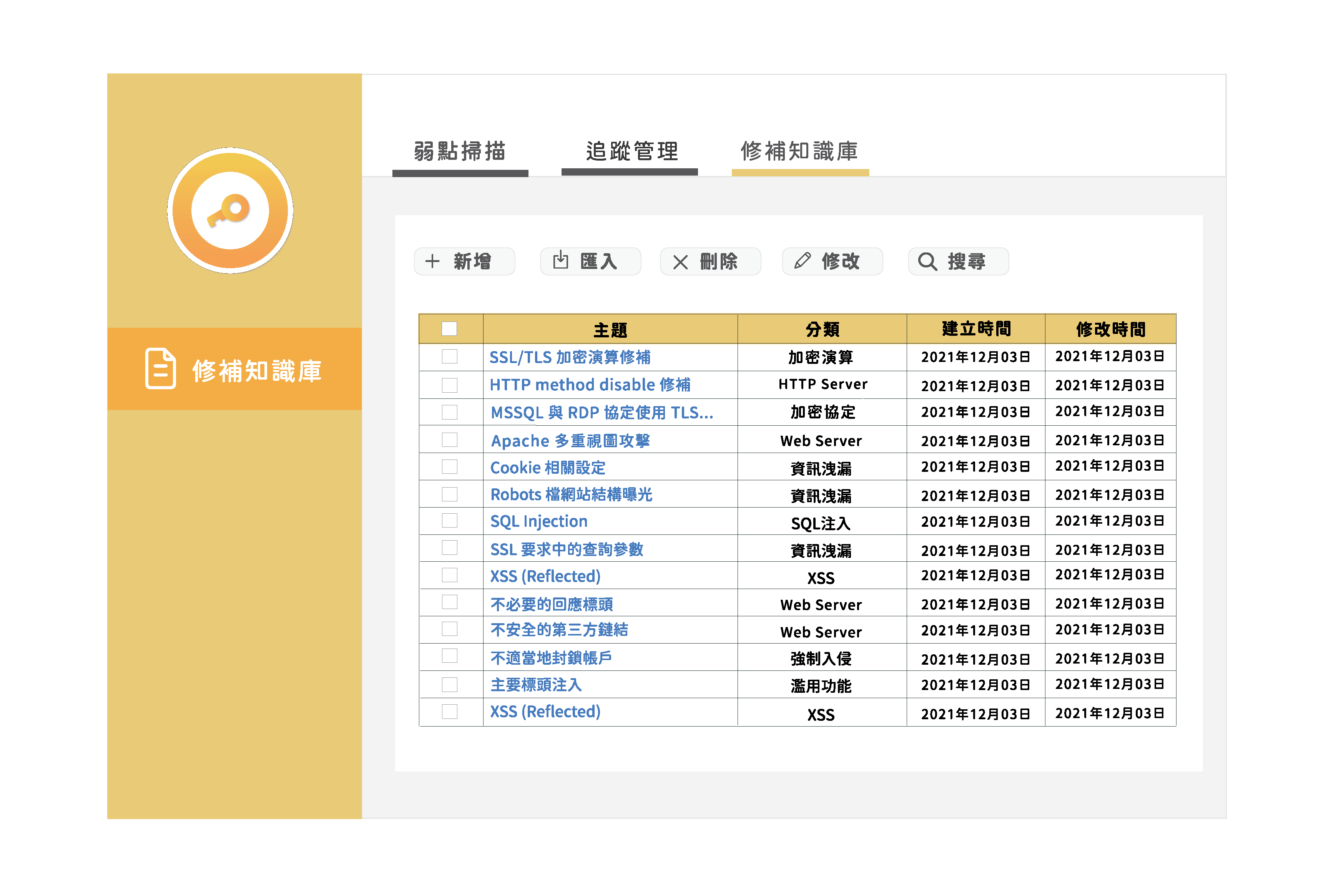
Key-Reporter has a built-in vulnerability knowledge base where users can directly look up suggestions for addressing vulnerabilities.